What are Trust Center Updates? Who receives these updates?
Trust Center Updates (TCUs) enable an organization to proactively communicate with their subscribers, both customers and prospects, by sharing relevant security-related information. These updates can be sent via email, your Trust Center, or both.
Below we highlight a handful of use cases - including rolling out a product security feature, the launch of your Trust Center, responding to a security incident, or informing customers of an updated SOC 2, among others. We provide examples of how SafeBase Trust Alliance members have leveraged these updates, as well as templates to get you started. We look forward to seeing your next Trust Center Update!
What are the different types of Trust Center Updates?
There are five different categories of Trust Center Updates:
- Compliance: Spotlight new compliance badges or documents uploaded (for example: a new SOC 2, Pentest, GDPR badge, etc.).
- Vulnerabilities: Inform customers about critical vulnerabilities in your application to encourage them to update as necessary.
- Incidents: Impact and remediation after an incident. Companies that are more transparent during incident response are more likely to maintain trust with customers after an incident. This label has also been used to provide statements on external vulnerabilities affecting commonly used software (for example: Log4j, OpenSSL, etc.).
- Subprocessor: Share new subprocessors that have been added, removed, or updated. Many data processing agreements require vendors to notify customers of changes in subprocessor usage.
- General: These include announcements after a Trust Center goes live, and program promotions (such as for bug bounty programs), among others.
1. Compliance

Examples:
- Acquia - SOC 2 Type 2 report now available
- Plaid - Renewed Certificate on Insurance (cyber) now available
- Hootsuite - Statement on CPRA
Template: Compliance Doc Update - (Short update)
Short and sweet, Trust Center Updates can be an opportunity to showcase your company’s personality, if you’d like. One or two sentences is all that’s needed to let your subscribers know the key details you’d like to share.
Title: New Compliance Documentation Now Available
Tag: Compliance
Body: We here at [Company] have just completed our latest audit for [ISO / SOC 2] [certification / compliance]! Documentation is now available in our Trust Center at https://trust[.]yourcompany[.]com
Template: SOC 2 Update
Keep it short or provide a lot of detail, the choice is yours. Remember that the audit period is always noted on the SOC 2 document itself, so whatever details you do not include here would easily be found by your customers. Additionally - you may choose to note that this is a recertification / re-attestation, showing your dedication to formal assessment of your program’s security posture.
Title: New SOC 2 Report Now Available
Tag: Compliance
Body: Our SOC 2 Type 2 report for the period of [date] to [date] is now available through our Trust Center.
Completion of the SOC 2 Type 2 audit demonstrates [Company]’s continued commitment to the security of our [Product name] product and that of our overall security posture.
Template: ISO Certification
Replace ISO 27001 with whatever respective certification your company holds. Make sure to note how that specific ISO certification demonstrates a specific achievement within your company.
Title: New ISO Certification
Tag: Compliance
Body: [Company] has recently achieved certification in ISO 27001, with our most recent certificate available for review in our Trust Center. ISO 27001 demonstrates our commitment to meet and exceed international information security standards.
More information is available here: [link to a public blog post and/or news article about the specific ISO certification, what it means, etc.]
Template: Privacy Notice
If applicable, you may want to highlight steps taken to ensure privacy while you have their attention, even if it’s a brief mention. To note, you may always refer to the Data Privacy card - best practice is to make sure this card is filled out within your Trust Center, that way customers don’t need to navigate away to another site for the info they need.
Title: Privacy Compliance Update - [Specific privacy law/reg here]
Tag: Compliance
Body: [Company] has conducted a full review of [the specific privacy law or regulation you’re choosing to highlight] and ensured that we are fully compliant.
Full details regarding how [Company] handles customer data are always available through our Privacy Policy at https://www[.]yourcompany[.]com/privacy
Template: SOC 2 In Progress
Just as important as sharing a completed SOC 2 attestation or ISO certification is demonstrating that an audit is underway. Most customers reevaluate vendors on an annual basis and proactively sharing that your annual SOC 2 audit is happening may prevent you from fielding unnecessary questions about when you may be publishing a new SOC 2 report.
Title: SOC 2 Audit In Progress
Tag: Compliance
Body: [Company] has just begun our annual SOC 2 Type 2 audit process. SOC 2 Type 2 compliance is an important part of how we attest to our security program’s strength here at [Company].
As we work with [the independent auditing firm] to articulate the various aspects of our security posture, we are happy to provide a bridge letter for any customers conducting vendor reviews during this time.
2. Vulnerabilities
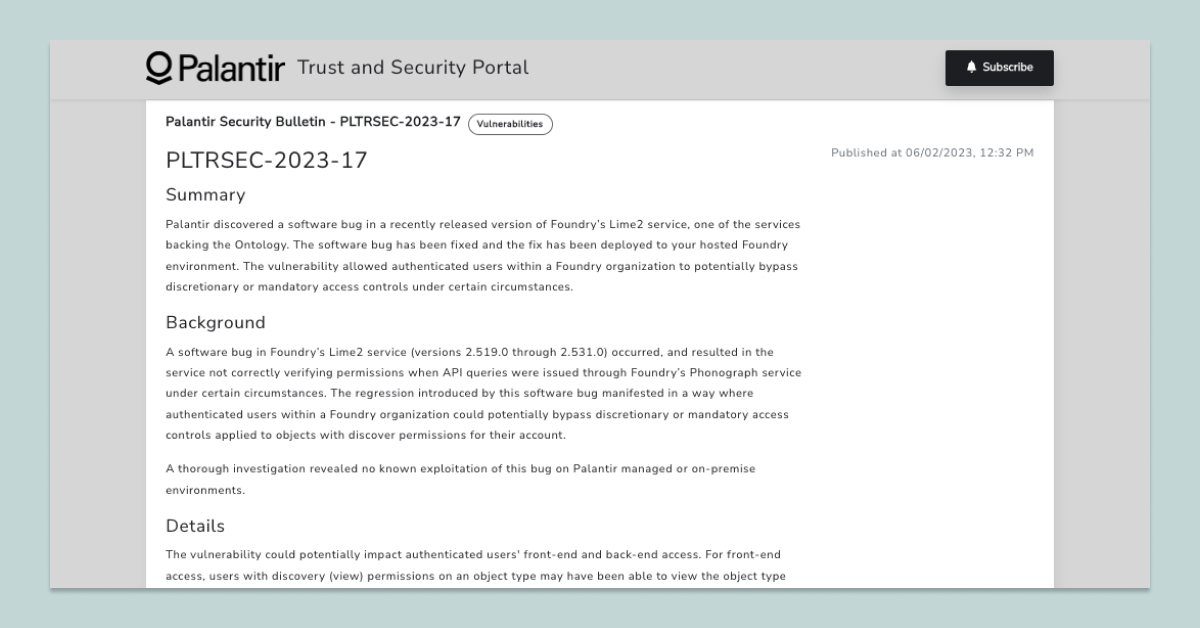
Examples: Palantir - Security bulletin for Foundry’s Lime2 Service
Template: Vulnerability Advisory
In advising existing customers of a vulnerability, you want to make clear how:
- You’re communicating proactively to them in a forward manner
- This is something you have already remediated with continuous improvement of product security
You may also choose to advertise your responsible disclosure channels, like bug bounty programs, or how you open your product to hacking conferences/research, etc.
Title: Vulnerability Advisory - [Company] [Product name]
Tag: Vulnerabilities
Body: [Company] recently discovered, through disclosure, that vulnerabilities exist within the [Product name] product. These vulnerabilities were brought to light through [background on how these were disclosed: bug bounty, hacking competitions, security research, etc.]. Links to additional information are below:
https://www[.]vulnerabilityinfo[.]com/yourinfohere
Action has already been taken by [Company] to remediate and patch these vulnerabilities. The purpose of this advisory is to keep our customers informed and aware of changes to our product, most importantly updates to the security of [Product name]. Additional testing has shown that these vulnerabilities no longer exist.
[Company] appreciates the efforts of those that helped with this responsible disclosure.
3. Incidents
Examples:
Template: Incident - Company Not Impacted - No Data Compromise
When there is a major vulnerability or incident that makes world news (think Log4j vulnerability or SolarWinds incident), all companies are wondering to what extent other companies are impacted. By reaching out proactively to say that you’re NOT impacted, you erase your company from the list of companies they should be worried about. At the same time, you build trust through transparency.
Title: [Company] Not Impacted by [Incident name]
Tag: Incidents
Body: On [exact date Company learned of incident], [Company] became aware of the [Incident name] security incident. Reputable threat intelligence sources have reported that this incident impacts [threat surface details here - link to relevant CVE, if available].
We want our customers to know that [Company] is not impacted by this vulnerability.
We do not leverage this technology/software within our product and therefore the confidentiality, integrity, and availability of our systems remain unharmed.
Template: Incident - Company Impacted - Potential Data Compromise
The goal here is to communicate:
- You’re transparent - yes, you were impacted, but you are responding diligently and as needed to ensure your customers are safe, as well as your own company.
- That you’re aware - you’re acknowledging what happened, have already taken necessary action, and are continuing to act.
- What the impact may be for your customers.
- Finally, what your next steps are. Be precise & clear on exactly what vulnerabilities you’re addressing. Make important language clear to customers through headings, italics, and/or bond font changes
Title: [Company] Update - [Incident name]
Tag: Incidents
Body: On [exact date Company learned of incident], [Company] became aware of the [Incident name] security incident. Reputable threat intelligence sources have reported that this incident impacts [threat surface details here - link to relevant CVE, if available].
[Company] maintains a number of security measures to monitor, investigate, and immediately respond to any and all incidents which may occur. Such measures allow us to control the impact and triage effectively. In the case of [Incident name], [in bold font - details regarding potential impact of incident against company data].
We will be sharing more updates as soon as they are available and as remediation efforts are ongoing.
[The last paragraph and/or statement should be language regarding next steps to be taken - perhaps when to expect the next update]
4. Subprocessors

Examples:
- EveryoneSocial - Subprocessor Changes Removal, Adding
- SafeBase - New Subprocessor Added: Flatfile
Template: New Subprocessor Added
Goals here:
- Be brief! Customers will want to know who the subprocessor is, what they do, and how you’ll be interacting with them. Basically, will they be impacted?
- Leverage the bullet points - Let them know you signed a DPA, let them know you completed your formal third-party risk management process
Title: [New Subprocessor name] - Subprocessor Added
Tag: Subprocessors
Body: As we work to continuously improve our product line and streamline our infrastructure, [Company] will now be engaging with [New Subprocessor name] to [describe service delivered here].
This serves as notice that [New Subprocessor name] is now a subprocessor of [Company].
Name: [New Subprocessor name]
Location: [country of service provided]
Website: subprocessorName[.]com
Purpose: [brief description of service to be delivered by new subprocessor]
DPA Signed: [Yes / No]
Third-Party Risk Evaluation Completed: [Yes / No]
This new subprocessor will be live as of [date of future service]. Please contact us with any questions or concerns.
Template: Existing Subprocessor Removed
Short and sweet! The addition of a subprocessor is more important - customers will want to know the who, what, why, and when. Here, the important detail is that you’re being transparent and proactive by communicating the removal of a subprocessor. All you need to do is share who you’re removing and when they were removed. Best practice is to always update public-facing subprocessor listings before any notices are shared externally.
Title: [Existing Subprocessor name] - Subprocessor Removed
Tag: Subprocessors
Body: In an effort to remain transparent with business partners and customers, [Company] is relaying this subprocessor removal notice to declare in our subprocessor list. We no longer rely on the services of [existing Subprocessor name] as of [past date of removal, if applicable].
This serves as notice that [existing Subprocessor name] is no longer within our subprocessor list.
To see the full list of our subprocessors, please visit the Legal card within our Trust Center (link).
5. General
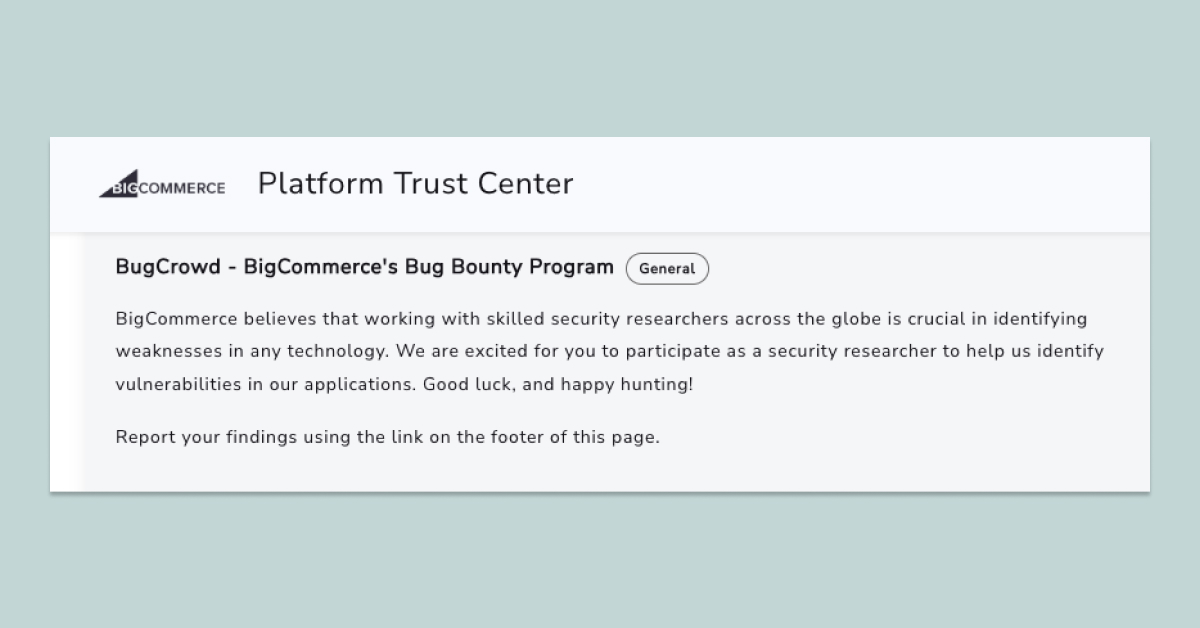
Examples:
- Harness - Welcome to the Harness Trust Center
- BigCommerce - Bug Bounty Program
- Thoropass - Official Name Change
- Snyk - Russia/Ukraine conflict update
- Livestorm - Unsolicited phone calls
Template: Launch of Trust Center
Title: Welcome to the [your company name] Security Trust Center
Tag: General
Body: As an organization that is security conscious and values security, we are excited to announce the official launch of the [your company name] Security Trust Center. By using this portal, you can request access to our compliance documents, review our standardized questionnaires such as the SIG and gain a general understanding of our security posture.
Over time, our team will be making changes to this portal as we implement new tools and processes in our environment. You can use the Subscribe button to receive email notifications for when our team has an important update, such as if we have an updated compliance report or if we have a status update regarding a major security vulnerability that has been recently discovered.
In Conclusion
We hope the above examples and templates are a helpful jumping off point. And if you are new to publishing TCUs, check out our step-by-step guide here to get started publishing your first one!
Lastly, we always love hearing from you. Did we miss any other categories or important topics that warrant a Trust Center Update? How else have you used TCUs? Let us know!
SafeBase is the scalable Trust Center that automates the security review process between buyers and sellers. With a SafeBase Trust Center, companies can seamlessly share sensitive security documentation with buyers and customers, including streamlining the NDA signing process by integrating with your CRM and your data warehouse.
If you’re ready to take back the time your team spends on security questionnaires, create a better buying experience, and position security as the revenue-driver it is, get in touch with us.


.jpeg)


.png)



